The concept of our solution doesn’t assume any completed set of measures for your (or your subscriber’s) system, however, we provide an integrated suite of security tools that provide all protecting functions you need in your particular case according to your threat environment and compliance requirements. So the set of SEA components protecting your service could be adapted through time by your growth, evaluation, and changing needs. Nevertheless, the scale of your enterprise and security features consumed you still can manage your own suite from a single point of control, simply switching on and off all your options due to real incident history and proven threats.
Security services should really get their job done, otherwise, why must you (or your subscribers) pay for them? Our approach provides you with a solid view of the service’s efficiency by reporting the number of attacks actually deflected, the number of assets really recovered, and a complete picture of your security level.
The current widespread of security issues and information security incidents forces one to use plenty of tools and configurations to achieve a secure state. But it reflects on the complexity and rapidly increases costs of your (or your subscriber’s) enterprise while remaining unclear about safety. The only way to free yourself from this trap is the subscription model when you use services as you need and can instantly receive it if it is needed, namely in your environment and if it simply provides any benefits - protects you from real or potential attacks.
Our solution provides integrated and ready-to-use security elements, such as firewall, integrity control, DDoS protector, patch management, and everything else that could be useful for you (or your subscribers) in the single simply manageable suite, when necessary services could be subscribed and unnecessary unsubscribed instantly.
Our essential conviction is that you (or your subscribers) should be focused on business but not on security issues and maintaining systems. We’d like to do that work for you! Using a trusted management channel we automatically provide all necessary security operations for you that you finally could always feel protected and secured. All service and policy updates are transparent for you and all you need to get the up to date information about your security level and your security measures effectiveness.
Being a subscriber you should use the single trusted point for all your operations including security. All security functions should be activated and priced through a custom portal. Our solution is integrated from the box with the most popular hosting providers platforms or could be rapidly adapted to your particular solution.
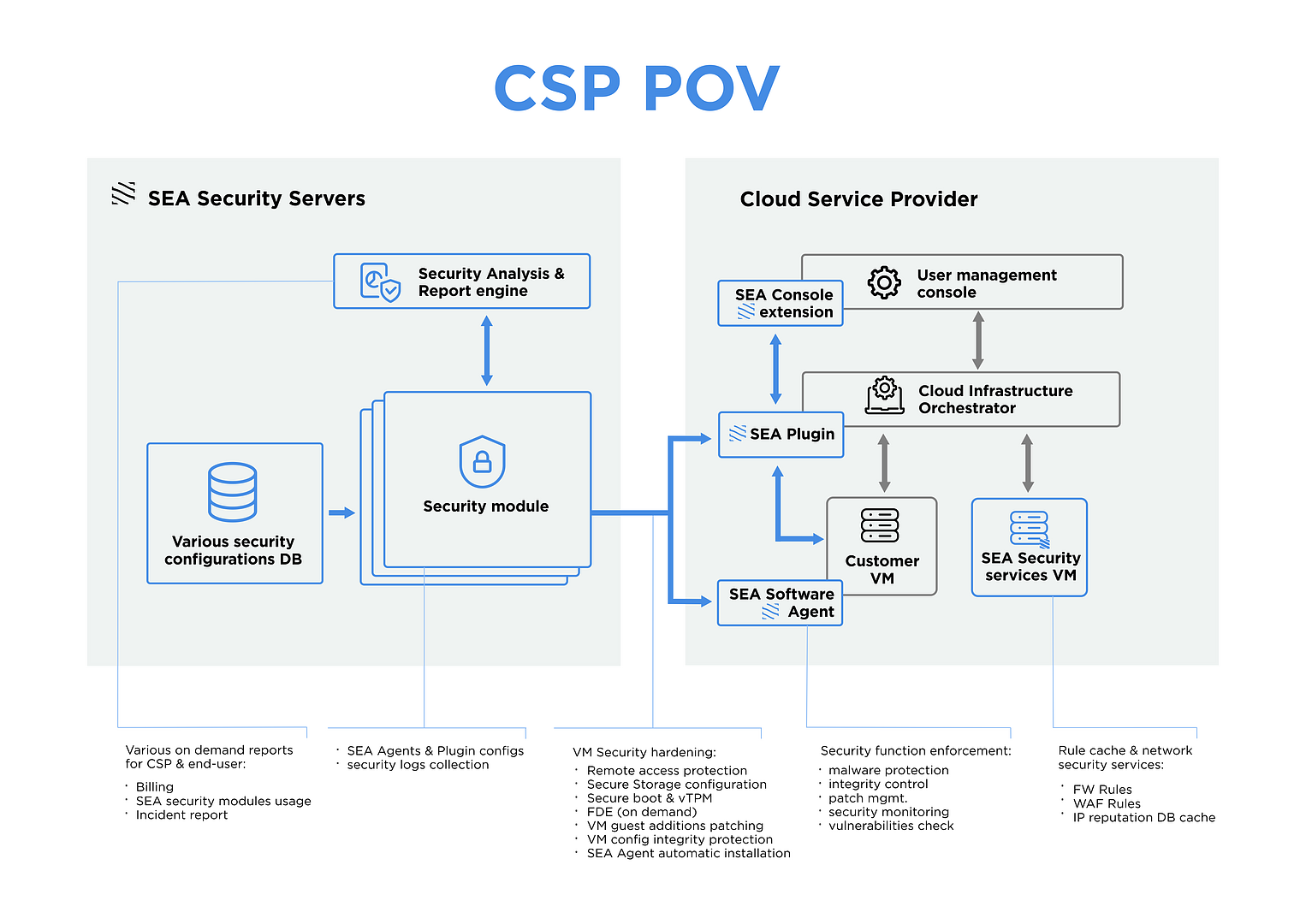
You can simply add the SEA security services to your service catalogue. All you need is to make sure that your cloud orchestration platform is supported by SEA. Next you need to install the SEA Plugin in your cloud orchestrator environment (or you can always use support from our engineer team for plugin installation). After that your clients will find a new menu entry at their management console – the SEA Security services. This menu will allow customers to harden their VM settings, give access to their VMs for SEA security modules and so on.
All security functions are implemented either by the SEA software agent installed in the guest environment or by a standard cloud service user’s console. All necessary configuration changes are just made automatically.
Additionally, we can provide a special SEA VM which will bring different rules databases closer to the user, which will greatly improve the user experience.
All secure configurations and rules are stored in our specifically designed security configuration database, which is constantly updated by our security team. You can be sure that we provide the most up-to-date configurations and rules for our security modules that will consider your platform’s individual features and user's VM templates.
Also you can receive on-demand reports with information about:
- SEA security modules usage statistics
- General incident reports
- Billing information
- …And much more
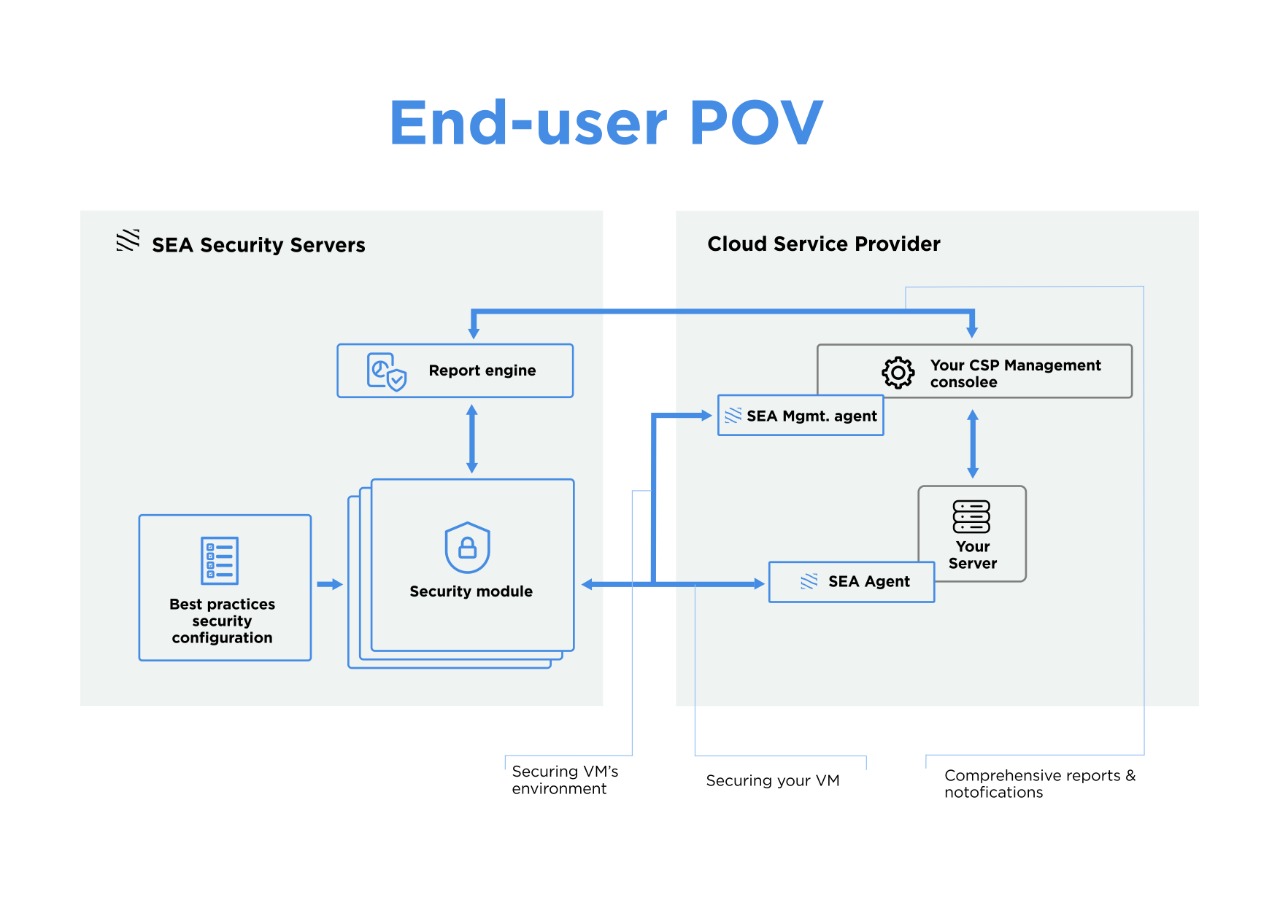
Adding security to your online services is very simple: you’ll find the SEA menu in your CSP Console where you can either choose security features you need or choose a function set best suited for your online service.
When you activate the SEA security service, you will be prompted to give the SEA management agent access to your service’s VMs. After that all the additional setup is made by the SEA management agent automatically. The SEA management agent will adjust your virtual environment configuration to come in line with best security practices for your CSP environment. Also the SEA management agent will install the SEA software agents into your VM’s guest environments. The SEA software agent will provide protection against malware infections and malicious user attacks.
All the SEA security service components use rules and configuration from our comprehensive security database, containing recommended security settings for all types of VMs and online services provided by it.
All SEA actions are performed automatically but completely transparent to you. You can always get on-demand reports of various detail levels: from the most general where only information about prevented attacks are shown, to detailed ones, where you can find the complete logs of SEA agent actions, raw security events and so on.
- Request a demo
- Request a trial
- Pricing
- Documentation
Solving security problems

Today we do not have to prove the reality of security issues. The permanently growing number of new security incidents absolutely proves it. The only question is how to get and organize all the features and functions which are useful for your subscribers? Putting the responsibility on their shoulders does not work due to reputation and moral issues. Unfortunately, most of your subscribers aren't able to solve these problems by themselves. Generating multiple problems, not only for their systems, but also for your ecosystem and maintaining costs. In addition to these problems, there are also questions concerning compliance and government regulations.
Obviously, you are able to implement your own security services, mixing popular and expensive tools into a highly custom difficult to manage solution. In addition, you will be forced in your own process of selling and proving the necessity of your tools for your subscribers. We are ready to give you a simple, integrated, and holistic solution, requiring zero capital costs and providing the additional ability for you to increase the RPu, stand out from competitors and finally provide provable security value for your customers. Using our solution excludes governmental compliance problems, increases the health of your ecosystem, and eliminates unnecessary costs, turning security from the problem into great capabilities.
Central management and billing

Our solution is capable of being integrated into most popular customer portal solutions such as Plesk, vstack, and cPanel. If you are using your own custom special solution, we are able to provide custom integration through API or additional integration modules. At the beginning of our collaboration we can provide you with a light interface to get your business integrated with our solution. You are just reselling our centralized manageable services for an additional fee until you decide to get us integrated into your custom portal, taking part in the management process providing your resources and receiving an additional value.
Central management and billing

Our solution is capable of being integrated into most popular customer portal solutions such as Plesk, vstack, and cPanel. If you are using your own custom special solution, we are able to provide custom integration through API or additional integration modules. At the beginning of our collaboration we can provide you with a light interface to get your business integrated with our solution. You are just reselling our centralized manageable services for an additional fee until you decide to get us integrated into your custom portal, taking part in the management process providing your resources and receiving an additional value.
Pay-as-you use model

We are providing a zero risk model for you, without extra costs to you, until your subscribers begin the full usage of our solution. Our portfolio includes a zero-cost trial and evaluation period until you start earning with our services. Both models are possible:
- After integration you are fully responsible for billing and paying for all your subscribers.
- When reselling our solution we receive payments from your subscribers, returning to you a percentage based on the trial period.
Other custom models are also possible according to your business needs.
Please feel free to contact us to discuss what works best for you.